In an era when cyber threats are more prevalent than ever, ensuring the security of web communication has become a top priority. One of the powerful tools in the arsenal of web security is HTTP Strict Transport Security, commonly known as HSTS. In this blog post, we’ll dive into what HSTS is, how it works, and why it’s crucial for safeguarding web applications and user data.
Understanding HSTS
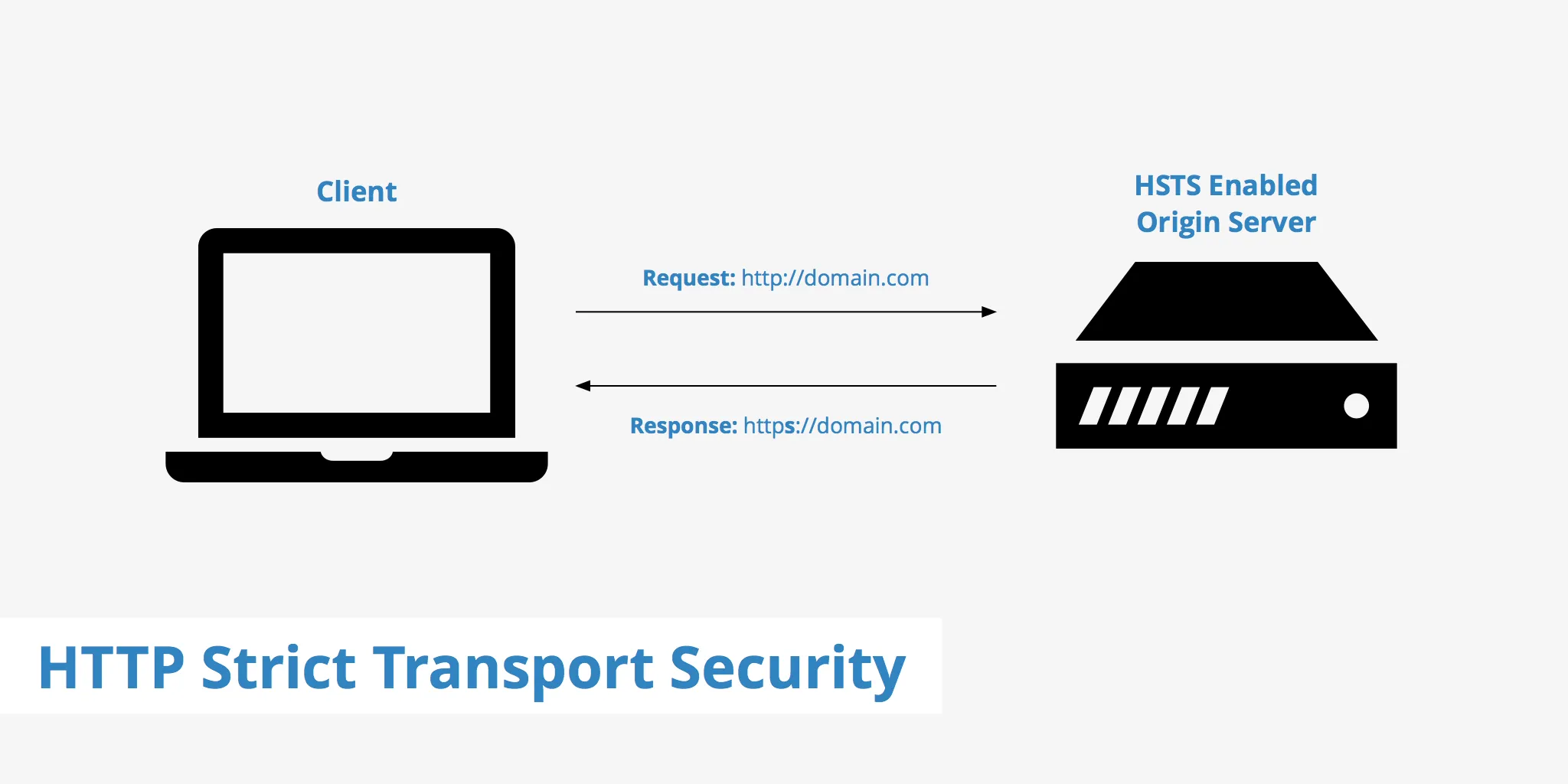
HTTP Strict Transport Security (HSTS) is a security policy mechanism that helps protect websites and web applications against certain types of attacks, particularly man-in-the-middle (MitM) attacks and SSL stripping. It achieves this by instructing web browsers to only connect to a given website using secure, encrypted HTTPS connections, effectively eliminating the possibility of unencrypted HTTP communication.
How HSTS Works
HSTS is implemented using HTTP response headers, which are sent by the web server to the client’s browser. Here’s how it works:
- Initial Connection: When a user first visits a website that supports HSTS, the web server responds with an HTTP header called “Strict-Transport-Security” in the response.
- HSTS Policy Declaration: This header contains several directives, including the most important one, “max-age,” which specifies the duration (in seconds) for which the HSTS policy should be enforced. During this time, the browser will automatically convert all HTTP requests for that domain to HTTPS, even if the user tries to enter “http://” in the URL bar.
- Subdomains: HSTS can be configured to apply to subdomains as well. If the “includeSubDomains” directive is set, the policy will also be applied to all subdomains of the main domain.
- Preloading: Websites can choose to be included in the HSTS preload list, which is a list of websites embedded in modern browsers. Once a website is preloaded, HSTS enforcement applies even for the first visit, ensuring maximum security.
Why HSTS is Crucial for Web Security
- Protection Against SSL Stripping: HSTS prevents attackers from downgrading secure HTTPS connections to insecure HTTP connections through techniques like SSL stripping. This is crucial in safeguarding sensitive data transmitted over the web.
- Mitigation of Man-in-the-Middle Attacks: MitM attackers intercept communications between users and websites. HSTS helps thwart these attacks by ensuring that all communications are encrypted.
- Improved User Trust: When users see the padlock icon (indicating a secure connection) in their browser, they are more likely to trust the website. HSTS helps maintain this trust by ensuring that secure connections are always established.
- Compliance with Security Standards: HSTS is recommended by security organizations like OWASP (Open Web Application Security Project) and is often considered a best practice in web security. Adhering to such standards is essential for protecting your website and complying with industry norms.
Implementing HSTS
Implementing HSTS is relatively straightforward:
- Configure your web server to include the “Strict-Transport-Security” header in its responses.
- Set the “max-age” directive to your desired duration (in seconds).
- Optionally, include the “includeSubDomains” directive if you want to apply HSTS to subdomains.
- Consider preloading your site in major browsers for maximum security.
Conclusion
HTTP Strict Transport Security (HSTS) is a robust security feature that offers significant protection against common web-based attacks. By enforcing secure HTTPS connections and mitigating the risk of SSL stripping and MitM attacks, HSTS enhances user trust and strengthens web application security. Web developers and administrators should consider implementing HSTS as an essential component of their security strategy to ensure the confidentiality and integrity of data transmitted over the web.